
|
Dissecting the NSA's 6-Step Playbook for Hacking Networks
Earlier this year an NSA executive named Rob Joyce gave a presentation on the six steps of targeted intrusions against nation states. We've put together an ebook discussing each step in the playbook, and how to protect yourself from hackers as sophisticated as the NSA.
Get The Ebook
|
|

|
A CIO's Perspective: You Can't Fix What You Can't See
ExtraHop CIO John Matthews relates a true story about a tiny database tweak causing a chain reaction that stopped his former employer from making sales for three hours. Hint: greater network visibility could have nipped the problem in the bud.
Read The Story
|
|

|
TCP_NODELAY: 2016 Best Practices for TCP Optimization
The TCP/IP stack is critical to every single business, and it is tough to keep it performing its best. Nagle delays, tinygrams, delayed ACK… it's a minefield! Read our thorough guide to best practices for TCP optimization, and make sure you're not wasting bandwidth that you could save just by toggling a socket setting.
Read the Guide
|
|

|
The Day The 'Net Stood Still
Remember a few weeks ago when a huge part of the internet was brought down by a colossal, Internet-of-Things-based DDOS attack? That sucked!
Understanding is the first step to stopping it from happening again. Check out this presentation on why IoT devices are so vulnerable, and how to gain better visibility into their activity to stop them from being used for evil!
Watch the Presentation
|
|
|
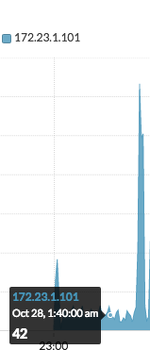
Interactive Demo: Seeing Data Theft Live on The Network
If hackers get into your network undetected, they're highly likely to try to move valuable or sensitive data off it to sell or use for their own purposes. If you can see into your network, especially internal "East-West traffic" within and between datacenters, it is easier to detect and prevent this data exfiltration.
Our interactive online demo walks you through a scenario of detecting and investigating data-exfiltration in action by examining suspicious spikes in ICMP traffic and other network data.
Check It Out
|
|

|
Rethink The Network: Giving Power and Context to All IT Roles
The network can literally (OK, figuratively) give everyone in your business superpowers. It is the best source of data, the most complete, thorough, and real-time way to get the info you need to make data-driven decisions across your organization. There's a digital transformation happening right now. The network is at its core. Do you know how to capitalize on it?
View Full Post
|
|

|
Log Data Fails When You Need It Most
Yeah, yeah, Mr. Robot is all the rage right now. But hackers have been in fiction for decades, and they've had real-world insights since the beginning. Neal Stephenson's Cryptonomicon had some of the most awesome hacking ever, and it was so incredibly realistic and relevant that it still matters. Read up on how this classic cyberpunk author understood the weakness of logs and the power of wire data way back in the day.
View Full Post
|
|
|

