| FEBRUARY 2018 |

|
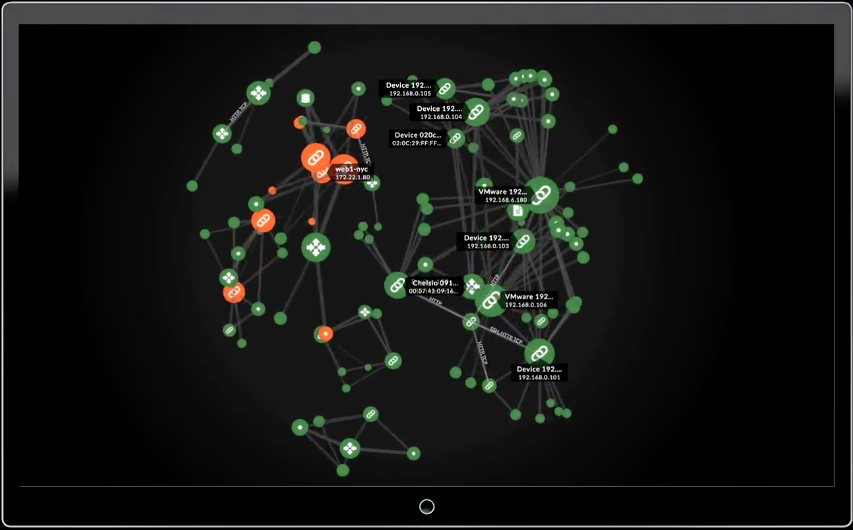
Your Risks, RevealedExtraHop Reveal(x) Changes the (Security) GameThere's a new security offering in town. On January 30th, ExtraHop unveiled our answer to alert fatigue and limited visibility: ExtraHop Reveal(x). Pairing advanced behavioral analytics with unprecedented internal visibility, ExtraHop Reveal(x) allows you to:
Short on time? This solution brief will bring you up to speed. |
a closer lookSilence Your Alert Cannons |
Better data leads to better outcomes. |
Work backwards for a better workflowIs Your Security Workflow Backwards?“What if you went to the supermarket, bought one of every item the store carried, paid for it all, searched through the items you purchased for the items you actually need, and subsequently returned the remaining items to the store?” It sounds ridiculous, but this is still how many companies treat security alerts. Our resident advisor Josh Goldfarb gives his two cents on optimizing your security strategy in this piece for DarkReading.
|
Protect your enterprise on all frontsDetect And Stop Ransomware With This ApproachTo proactively identify and control ransomware, organizations don't just need to control the perimeter (north-south traffic), they need real-time visibility into communications within their networks (east-west traffic). This white paper offers observations and tested methods on how ExtraHop can effectively neutralize ransomware. From this paper, you'll learn:
|

|
What's Next? |
February 15 - 21 February 26 - 28 March 5 - 9 |
Good ReadsWelcoming a New Member of the Family: ExtraHop Reveal(x) 3 Reasons You Need a Data Center Consolidation Strategy |
Dive DeeperSolutions Bundles: Threat Identification Online Training: |
|
|
|